Reverse DNS Lab (IPv6)
Note: IPv6 subneting understanding is required here.
Check your IPv4 rDNS prefix. E.g for attendee 01 it is: 2001:470:702c:a01::/64.
First, for simplicty and sake of understanding make sure to write all leading zeros. Thus 470 becomes 0470, a01 becomes 0a01.
2001:0470:702c:0a01::/64.
Next, write entire first 4 octets (our network bits) in reverse:
| Octet | Forward | Reversed |
|---|---|---|
| First | 2001 | 1002 |
| Second | 0470 | 0740 |
| Third | 702c | c207 |
| Fourth | 0a01 | 10a0 |
Next, add dots between each reverse value:
| Octet | Reversed | With dots |
|---|---|---|
| First | 1002 | 1.0.0.2 |
| Second | 0740 | 0.7.4.0 |
| Third | c207 | c.2.0.7 |
| Fourth | 10a0 | 1.0.a.0 |
Next, write the zone in reverse i.e forth-octet.third-octet.second-octet.first-octet.ip6.arpa.
1.0.a.0.c.2.0.7.0.7.4.0.1.0.0.2.ip6.arpa.
Add this in PowerDNS admin by clicking on “Create Zone”
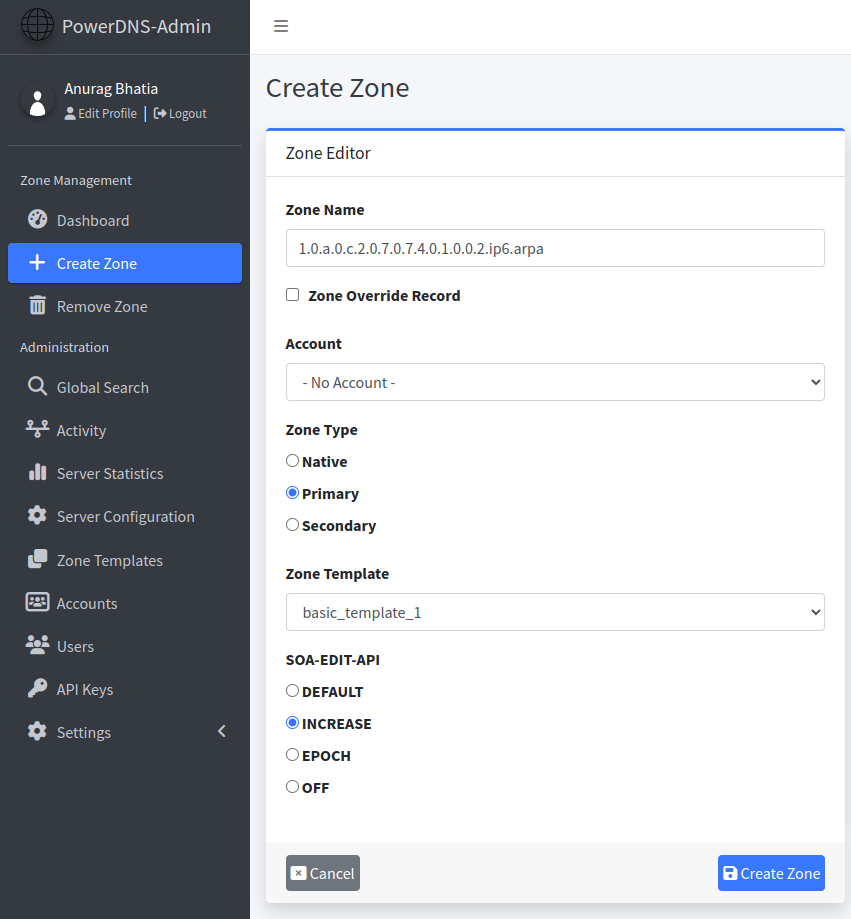
Create following two records:
- Point 1st IP (2001:470:702c:a01::1) to - mail.bom.my-domain.com.
- Point 2nd IP to (2001:470:702c:a01::2) - router.bom.my-domain.com.
Select “Zones ip6.arpa” from the top tab and open the respective zone:
Next, determine record value. E.g 2001:470:702c:a01::1 can be expanded as: 2001:0470:702c:0a01:0000:0000:0000:0001. We are already inside the /64 zone (out of 128 bits) thus next 64 bits are address size here:
2001:0470:702c:0a01:0000:0000:0000:0001 = 2001:0470:702c:0a01 (network bits) + 0000:0000:0000:0001 (host bits). Write host bits in reverse:
1000:0000:0000:0000 and next add . in between:
1.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0 <- This is record value.
dig for record you want to create with -x and look at expanded question section:
e.g for 2001:470:702c:a01::1
anurag@desktop ~> dig -x 2001:470:702c:a01::1
; <<>> DiG 9.18.18-0ubuntu2.1-Ubuntu <<>> -x 2001:470:702c:a01::1
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: SERVFAIL, id: 31383
;; flags: qr rd ra; QUERY: 1, ANSWER: 0, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 65494
;; QUESTION SECTION:
;1.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.1.0.a.0.c.2.0.7.0.7.4.0.1.0.0.2.ip6.arpa. IN PTR
;; Query time: 1280 msec
;; SERVER: 127.0.0.53#53(127.0.0.53) (UDP)
;; WHEN: Sat Apr 20 06:45:15 IST 2024
;; MSG SIZE rcvd: 101
anurag@desktop ~>
Remove the zone part (1.0.a.0.c.2.0.7.0.7.4.0.1.0.0.2.ip6.arpa.) to get the record value: 1.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0
Click “+ Add record” and put “1.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0” in the name for first or “2.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0” for second. Click “Save” for each record and “Save changes” on the top to push changes to the auth DNS server.
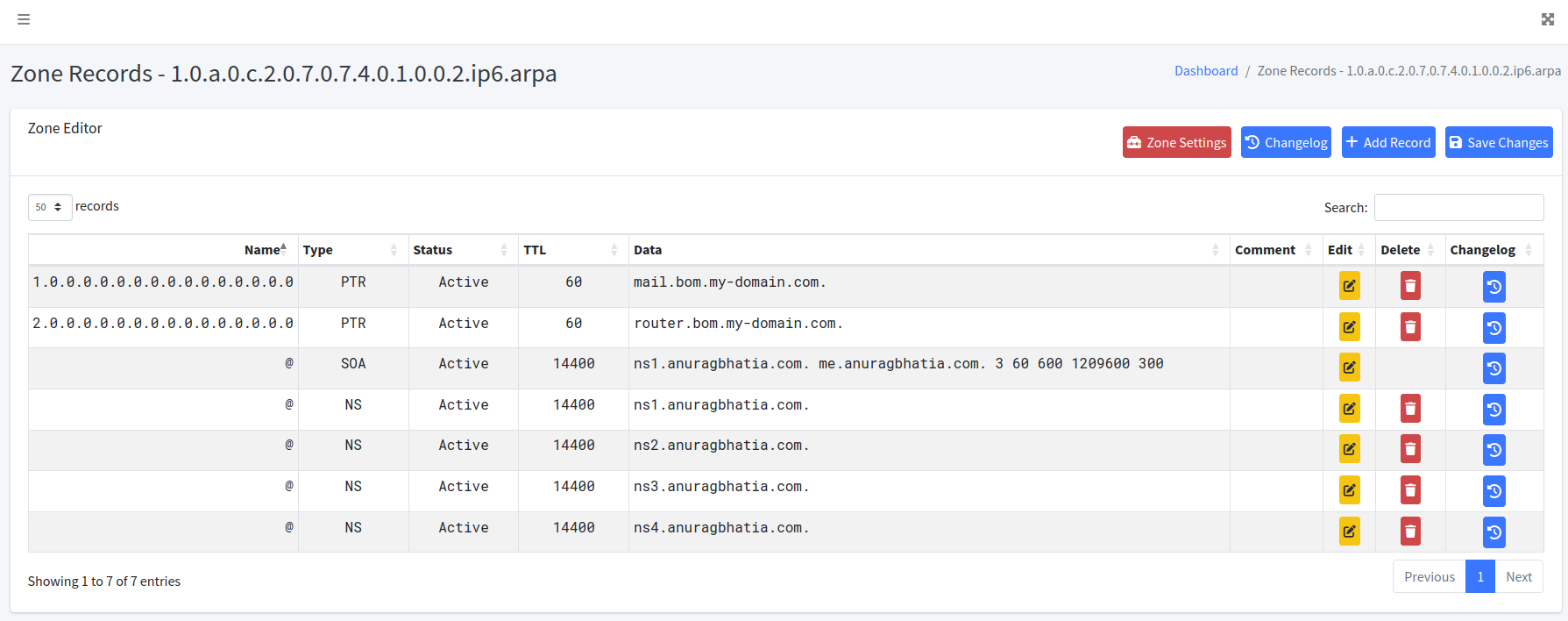
Once added, query your primary or secondary auth server directly (due to IPv4 limitation) and verify that you see records.
anurag@desktop ~> dig -x 2001:470:702c:a01::1 @ns1.anuragbhatia.com +short
mail.bom.my-domain.com.
anurag@desktop ~>
anurag@desktop ~> dig -x 2001:470:702c:a01::2 @ns1.anuragbhatia.com +short
router.bom.my-domain.com.
anurag@desktop ~>